The Big Picture |
- Two Sentences that Explain the Crisis and How Easy it Was to Avoid
- How Much Is the US Government Spying On Americans?
- Mind Over Mechanics
- 10 Thursday PM Reads
- P&I 2013: Largest Money Managers
- Advance Declines Break Out to New Highs
- Kudlow: Bernanke Was Right!
- 10 Thursday AM Reads
- Hedge Fund Dysfunction Syndrome
- The Fraud of the Prince of Poyais
- Solved: UFOs, Loch Ness Monster, Ghosts & Bigfoot
- Common Stock Repurchases during the Financial Crisis
| Two Sentences that Explain the Crisis and How Easy it Was to Avoid Posted: 12 Jul 2013 02:00 AM PDT Two Sentences that Explain the Crisis and How Easy it Was to Avoid
Everyone should read and understand the implications of these two sentences from the 2011 report of the Financial Crisis Inquiry Commission (FCIC). "From 2000 to 2007, [appraisers] ultimately delivered to Washington officials a petition; signed by 11,000 appraisers…it charged that lenders were pressuring appraisers to place artificially high prices on properties. According to the petition, lenders were 'blacklisting honest appraisers' and instead assigning business only to appraisers who would hit the desired price targets" (FCIC 2011: 18). Those two sentences tell us more about the crisis' cause, and how easy it was to prevent, than all the books published about the crisis – combined. Here are ten key implications.
|
| How Much Is the US Government Spying On Americans? Posted: 11 Jul 2013 10:30 PM PDT Anyone Who Says the Government Only Spies On Potential Bad Guys Is WRONGEven now – after all of the revelations by Edward Snowden and other whistleblowers – spying apologists say that the reports are "exaggerated" or "overblown", and that the government only spies on potential bad guys. In reality, the government is spying on everyone's digital and old-fashioned communications. For example, the government is photographing the outside information on every piece of snail mail. The government is spying on you through your phone … and may even remotely turn on your camera and microphone when your phone is off. As one example, the NSA has inserted its code into Android's operating system … bugging three-quarters of the world's smartphones. Google – or the NSA – can remotely turn on your phone's camera and recorder at any time. Cell towers track where your phone is at any moment, and the major cell carriers, including Verizon and AT&T, responded to at least 1.3 million law enforcement requests for cell phone locations and other data in 2011. (And – given that your smartphone routinely sends your location information back to Apple or Google – it would be child's play for the government to track your location that way.) Your iPhone, or other brand of smartphone is spying on virtually everything you do (ProPublica notes: "That's No Phone. That's My Tracker"). The government might be spying on you through your computer's webcam or microphone. The government might also be spying on you through the "smart meter" on your own home. The FBI wants a backdoor to all software. But leading European computer publication Heise said in 1999 that the NSA had already built a backdoor into all Windows software. And Microsoft has long worked hand-in-hand with the NSA and FBI so that encryption doesn't block the government's ability to spy on users of Skype, Outlook, Hotmail and other Microsoft services. (And leading security experts say that the NSA might have put a backdoor in all encryption standards years ago. … meaning that the NSA can easily hack into encrypted communications.) "Black boxes" are currently installed in between 90% and 96% of all new cars. And starting in 2014, all new cars will include black boxes that can track your location. License plate readers mounted on police cars allow police to gather millions of records on drivers … including photos of them in their cars. A security expert and former NSA software developer says that hackers can access private surveillance cameras. Given that the NSA apparently already monitors public cameras using facial recognition software, and that the FBI is building a system which will track "public and private surveillance cameras around the country", we can assume that government agencies might already be hacking into private surveillance cameras. The CIA wants to spy on you through your dishwasher and other "smart" appliances. As Slate notes:
And they're probably bluffing and exaggerating, but the Department of Homeland Security claims they will soon be able to know your adrenaline level, what you ate for breakfast and what you're thinking … from 164 feet away. (In addition, people will probably soon be swallowing tracking devices for medical purposes) The government is allegedly scanning prisoners' brains without their consent at Guantanamo. In the near future, brain scanners may be able to literally read our thoughts (and see this). The government is currently testing systems for use in public spaces which can screen for "pre-crime". As Nature reports:
CBS News points out:
The risk of false positives is very real. As Computer World notes:
Various "pre-crime" sensing devices have already been deployed in public spaces in the U.S. The government has also worked on artificial intelligence for "pre-crime" detection on the Web. And given that programs which can figure out your emotions are being developed using your webcam, every change in facial expression could be tracked. According to the NSA's former director of global digital data – William Binney – the NSA's new data storage center in Utah will have so much storage capacity that:
The NSA is building next-generation quantum computers to process all of the data. NBC News reports:
This includes metadata … which can tell the government a lot about you. And it also includes content. The documents leaked by Edward Snowden to Glenn Greenwald show:
In addition, a government expert told the Washington Post that the government "quite literally can watch your ideas form as you type." A top NSA executive confirmed to Washington's Blog that the NSA is intercepting and storing virtually all digital communications on the Internet. McClatchy notes:
NSA whistleblower Russel Tice – a key source in the 2005 New York Times report that blew the lid off the Bush administration's use of warrantless wiretapping – says that the content and metadata of all digital communications are being tapped by the NSA. The NSA not only accesses data directly from the largest internet companies, it also sucks up huge amounts of data straight from undersea cables providing telephone and Internet service to the United States. After all, the government has secretly interpreted the Patriot Act so that "everything" is deemed relevant … so the government can spy on everyone. The NSA isn't the only agency which is conducting massive spying. The Wall Street Journal notes:
Reason notes:
Even if the US government weren't recording all of that data, England's GCHQ spy agency is … and is sharing it with the NSA. Germany, Australia, Canada and New Zealand are also recording and sharing massive amounts of information with the NSA. Private contractors can also view all of your data … and the government isn't keeping track of which contractors see your data and which don't. And because background checks regarding some contractors are falsified, it is hard to know the types of people that might have your information. And top NSA and FBI experts say that the government can retroactively search all of the collected information on someone since 9/11 if they suspect someone of wrongdoing … or want to frame him. The American government is in fact collecting and storing virtually every phone call, purchases, email, text message, internet searches, social media communications, health information, employment history, travel and student records, and virtually all other information of every American. The Wall Street Journal reported that the NSA spies on Americans' credit card transactions. Many other government agencies track your credit card purchases as well. As Washington Monthly noted in 2004, Congress chopped off the head of the Total Information Awareness program … but the program returned as a many-headed hydra:
Senators Wyden and Udall – both on the Senate Intelligence Committee, with access to all of the top-secret information about the government's spying programs – write:
In fact, all U.S. intelligence agencies – including the CIA and NSA – are going to spy on Americans' finances. The IRS will be spying on Americans' shopping records, travel, social interactions, health records and files from other government investigators. The government is flying drones over the American homeland to spy on us. Indeed, the head of the FBI told Congress that drones are used for domestic surveillance … and that there are no rules in place governing spying on Americans with drones. Senator Rand Paul correctly notes:
Emptywheel notes in a post entitled "The OTHER Assault on the Fourth Amendment in the NDAA? Drones at Your Airport?":
Many police departments are also using drones to spy on us. As the Hill reported:
The military is paying for the development of drones with facial recognition software which "remember" people's faces … and read "malintent". Moreover, Wired reports:
RT notes:
The TSA has moved way past airports, trains and sports stadiums, and is deploying mobile scanners to spy on people all over the place. This means that traveling within the United States is no longer a private affair. You might also have seen the news this week that the Department of Homeland Security is going to continue to allow searches of laptops and phones based upon "hunches". What's that about? The ACLU published a map in 2006 showing that nearly two-thirds of the American public – 197.4 million people – live within a "constitution-free zone" within 100 miles of land and coastal borders:
The ACLU explained:
Computer World reports:
Wired pointed out in 2008 that the courts have routinely upheld such constitution-free zones:
Do you still believe that the government is only spying on bad guys in "targeted" searches? |
| Posted: 11 Jul 2013 05:00 PM PDT The future is here: In a jaw-dropping feat of engineering, electronics turn a person’s thoughts into commands for a robot. Using a brain-computer interface technology pioneered by University of Minnesota biomedical engineering professor Bin He, several young people have learned to use their thoughts to steer a flying robot around a gym, making it turn, rise, dip, and even sail through a ring. The technology may someday allow people robbed of speech and mobility by neurodegenerative diseases to regain function by controlling artificial limbs, wheelchairs, or other devices. And it’s completely noninvasive: Brain waves (EEG) are picked up by the electrodes of an EEG cap on the scalp, not a chip implanted in the brain. A report on the technology has been published in the Journal of Neural Engineering: http://iopscience.iop.org/1741-2552/10/4/046003/article |
| Posted: 11 Jul 2013 01:30 PM PDT My afternoon train reading:
What are you reading?
|
| P&I 2013: Largest Money Managers Posted: 11 Jul 2013 11:30 AM PDT Pensions & Investments Magazine's 2013 Special Report on AUM rankings are strangely fascinating
TOP MONEY MANAGERS
TOP INSTITUTIONAL MONEY MANAGERS
|
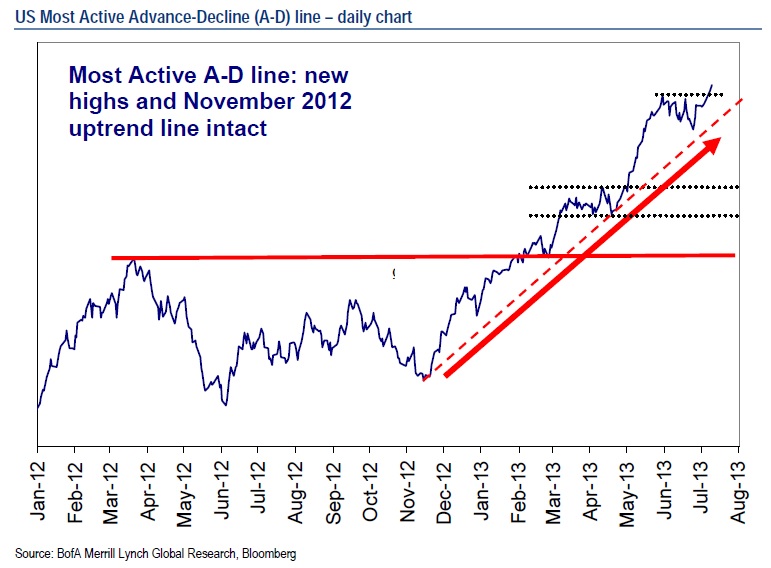
| Advance Declines Break Out to New Highs Posted: 11 Jul 2013 09:30 AM PDT
From Merrill Lynch’s technical team:
Source: |
| Posted: 11 Jul 2013 08:30 AM PDT Click for video |
| Posted: 11 Jul 2013 07:00 AM PDT My morning reads:
What are you reading?
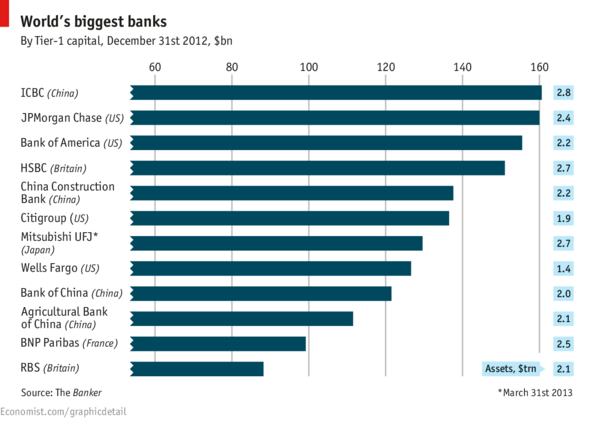
Banking behemoths |
| Hedge Fund Dysfunction Syndrome Posted: 11 Jul 2013 03:30 AM PDT
Ron Burgundy says: Stay classy, Businessweek!
|
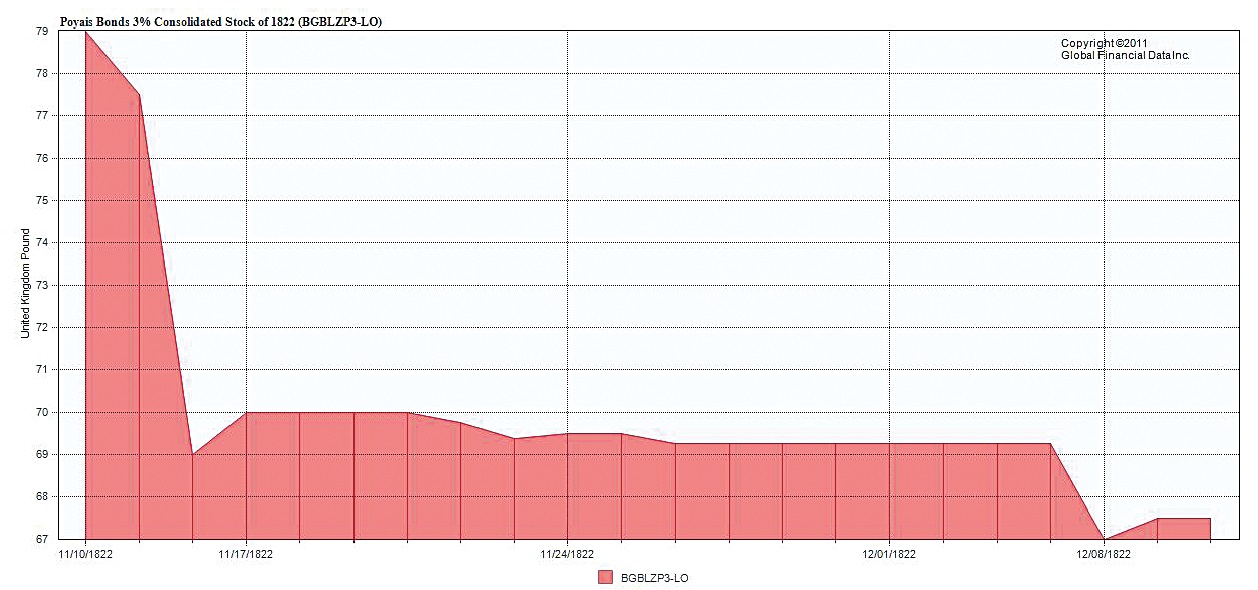
| The Fraud of the Prince of Poyais Posted: 11 Jul 2013 03:00 AM PDT Dr. Bryan Taylor is Chief Economist of Global Financial Data. ~~~ Charles Ponzi built the original Pyramid scheme; Michael Milken sold junk bonds; Nick Leeson was the rogue trader who broke Barings Bank; and Bernie Madoff bilked investors with trading that did not exist. All of these men were un-ambitious amateurs when compared to Gregor McGregor, the financial fraudster to top all fraudsters. Gregor McGregor was a very selfish swindler who returned nothing to any of his investors. At least Bernie Madoff and Charles Ponzi took some of the money they received from investors and returned it to perpetuate their Ponzi scheme, but Gregor McGregor kept all the money for himself. He also granted himself the title of Sir, as well as, Grand Cazique (Prince) of Poyais indicating his extreme self-confidence and narcicism. It is one thing to convince investors to invest money in a company that The South American Bubble
Gregor McGregor had joined the Royal Navy in 1803 and was a Colonel in the Venezuelan War of Independence, fighting under Simon Bolivar who had fought in Florida in 1817. In 1820, he returned to London and announced that had been named the Cacique (Prince) of the Principality of Poyais. The country was located on the Bay of Honduras and the land had been allegedly bestowed upon him by native chief King Frederic Augustus I of the Mosquito Shore and Nation. The country included over 12,500 square miles of untapped, rich lands which only lacked settlers to develop. To help promote his cause, he published a book, Sketch of the Mosquito Shore, including the Territory of Poyais, supposedly written by Captain Thomas Strangeways. The book said English settlers had founded the capital of St. Joseph in the 1730s, had untapped gold and silver mines, In reality, King Frederic Augustus had signed the document granting the land to Gregor McGregor in April 1820 after being plied with whiskey and rum. The land only had four run-down buildings in it, and was surrounded The Assets of Poyais? Once people began to read about the Territory of Poyais and all of its riches, investors had the misfortune to meet with the Cacique of Poyais in London's inner circles of the rich and famous. For the rich he offered 2000 bonds at £100 each on October 23, 1822, which resulted in £200,000 in sales. The bonds were offered at 80 and paid 3% interest. For the poor, he offered land for sale at the rate of 3 shillings, 3 pence per acre (later 4 shillings), which was about a day's wages in 1822, therefore it appeared to be a very attractive investment. He sold places in his military, the right to be shoemaker to the Princess, a jeweler, teacher, clerk or other craftsmen in his non-existent government and country. In fact, he even issued his own currency which the settlers could use once they arrived in Gregor McGregor's El Dorado. The Poyaisian Legation to Britain opened offices in London, and land offices were opened in Glasgow, Stirling and Edinburgh to sell land to his fellow Scots. Gregor McGregor had a group of people who promoted and sold all the land and other Poyaisian goods, sharing the profits with McGregor. By 1823, Gregor McGregor was a multi-millionaire in today's terms. The Settlement of Poyais As amazing as it may seem, the Legation of Poyais chartered two boats to take settlers to Poyais. Why they would take this risk, knowing that the settlers would discover the truth about Poyais once they arrived, staggers the imagination, but perhaps the fraudster had started to believe his own fraud. On September 10, 1822, the Honduras Packet departed from London with 70 settlers including doctors, lawyers and a banker. On January 22, 1823, the Kennersley Castle left Leith Harbour in Scotland with almost 200 settlers. When they arrived in Poyais, the settlers, some of whom had risked their life savings, found an uninhabitable jungle that had more tropical diseases than silver and gold. Of the original 240 settlers who reached Poyais, only 60 survived. The rest died. The Mexican Eagle, an official ship from British Honduras happened upon the Poyaisian settlers in April 1823 and brought King George Frederic to the settlers to tell them he had revoked the land grant because McGregor had assumed sovereignty. Fifty settlers sailed back to London on the Ocean on August 1, 1823 and arrived in London on October 12, 1823. The next day, the story of the ill-fated investors hit the newspapers of London. Amazingly, many of the settlers defended Gregor McGregor, believing the Cacique had been duped. One of the settlers, James Hastie, who lost two children to tropical diseases, published a book Narrative of a Voyage in the Ship Kennersley Castle from Leith Roads to Poyais, in which he blamed his advisors and publicists for the false information about Poyais. Gregor McGregor, however, fled to France Gregor McGregor's Later Once in France, Gregor McGregor continued his fraud. He wrote a constitution for the Republic (no longer a Principality) of Poyais and tried to sell land to French settlers. In 1825, he tried to issue new bonds, and shares in a Poyaisian company. When potential settlers began applying to the French authorities to sail to a country that didn't exist, the French began investigating. Gregor McGregor was arrested on December 7, 1825 and spent two months in prison on remand. There were two trials, one in April 1826 and another in July 1826 in which McGregor was acquitted, but one of his co-conspirators, Lehuby was sentenced to 13 months in prison. Gregor McGregor returned to London, and still claiming to be the Cacique of the Republic of Poyais opened an office at 23 Threadneedle Street (near the Bank of England). He tried to issue new Poyais bonds in 1827 through Thomas Jenkins and Company as brokers, but with little success. In 1828 he tried to sell land in Poyais at 5 shillings an acre (about $1). In 1839, Gregor McGregor moved to Venezuela where he received a pension as a general who had fought in the Venezuelan War of Independence. He died on December 4, 1845. The history of Poyais and Gregor McGregor should forever remain a cautionary tale to investors. Don't believe every "hot" opportunity that comes your way because history indicates that we will encounter another clever swindler. May investors beware so that they do not fall prey of the next Cacique.
Source: |
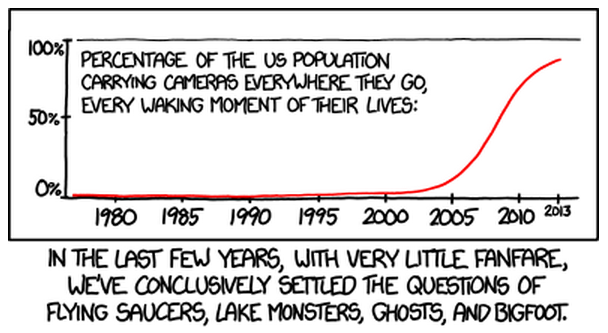
| Solved: UFOs, Loch Ness Monster, Ghosts & Bigfoot Posted: 11 Jul 2013 02:30 AM PDT |
| Common Stock Repurchases during the Financial Crisis Posted: 11 Jul 2013 02:00 AM PDT Common Stock Repurchases during the Financial Crisis
Large bank holding companies (BHCs) continued to pay dividends to their shareholders well after the onset of the recent financial crisis. Academics, industry analysts, and policymakers have noted that these payments reduced capital at these firms at a time when there was considerable uncertainty about the full extent of losses facing individual banks and the banking industry. But dividends are not the only means to return capital to shareholders; stock repurchases serve much the same function. In this post, I examine common stock repurchases by large BHCs during the financial crisis and show that they behaved very differently from common stock dividends during the same period. While dividends remained relatively constant through late 2008, common stock repurchases dropped quickly after the beginning of the financial crisis, consistent with their historically tighter sensitivity to current performance and financial conditions. BHC Dividends during the Financial Crisis Many analysts and researchers have noted that large BHCs did not reduce common stock dividends until the financial crisis was well under way. For instance, in a study examining capital at large U.S. and European banks, securities firms, and U.S. government-sponsored enterprises, Acharya, Gujral, Kulkarni, and Shin show that dividends at these firms did not decrease significantly until early 2009. In an October 2008 New York Times op-ed piece, Scharfstein and Stein argued that dividend payments by the largest U.S. BHCs would "redirect more than $25 billion of the $125 billion [in TARP capital] to shareholders in the next year alone." Both sets of authors argued that continued high dividend payments undercut the capitalization of the U.S. banking industry during a time of stress. In 2011, the Federal Reserve implemented the Comprehensive Capital Analysis and Review (CCAR) to review planned dividend payments and other capital distributions by large BHCs to ensure that they would retain sufficient capital to withstand stressed economic and financial market conditions even after making such distributions to shareholders (see my earlier post for a description of how the CCAR addresses this objective). Regulatory report data confirm the findings about dividends from these earlier studies. The first chart (below) shows the quarterly history of dividends declared by large U.S. BHCs—those with at least $10 billion in assets—from 2005 to the end of 2009. This period starts two years before the onset of the crisis in mid-2007 and extends until the beginning stages of the recovery at the end of 2009. (For consistency over the period, the sample excludes the large nonbank financial firms that became BHCs in early 2009.) As the chart shows, large BHCs made dividend payments in the range of $9 billion to $12 billion per quarter from 2005 to 2007, and while dividends declined over the course of 2008, they did not fall significantly below this level until early 2009, more than a year into the financial crisis.
Dividends Are Not the Whole Story The second chart (below) updates the first one to include common stock repurchases for the sample of large BHCs. Both dividend and repurchase information come from the quarterly FR Y-9C regulatory reports, which contain balance sheet and income statement information for BHCs. While the Y-9C reports collect dividends declared as a distinct line item, repurchases are not reported directly and must be inferred from other information contained in the report. For the second chart, I've used BHC purchases of treasury stock—common stock issued but not held by the public—as a proxy for common stock repurchases. This is a noisy measure of repurchases, as it may omit some repurchase activity that is reported as part of other Y-9C line items. However, it is a reasonable proxy that should capture the broad movements in repurchase activity.
The second chart illustrates several notable aspects of repurchase activity by large BHCs. First, in the period leading up to the financial crisis, stock repurchases were significant, averaging $7.5 billion per quarter and peaking at $12 billion in the first quarter of 2007. Stock repurchases were about two-thirds the size of dividend payments over this period, meaning that total distributions to shareholders were substantially higher than indicated by considering dividends alone. This is not something new in the banking industry. Some of my earlier research, which examined BHC stock repurchases during the 1990s, also found that stock repurchases rivaled dividends as a way for BHCs to return capital to shareholders. Second, share repurchases dropped sharply during the early phases of the financial crisis, several quarters before dividends were significantly reduced. Stock repurchases by large BHCs fell from their peak of $12 billion in the first quarter of 2007 to about $2 billion during the first quarter of 2008, and were at negligible levels after the middle of that year. As noted above, dividends did not decrease significantly until early 2009. Because of the decline in repurchases, large BHCs' overall capital distributions to shareholders declined steadily over the course of 2007 and 2008, a somewhat different picture than the one that emerges by looking at dividends alone. By the beginning of 2008, overall capital distributions had fallen below the levels that prevailed during the pre-crisis period. Even so, as the second chart illustrates, it was not until early 2009, when dividends also declined sharply, that overall distributions fell to the very low levels that ultimately prevailed for the remainder of the financial crisis and the period that followed. Why Are Repurchases Different? Much further research is needed to come to a full understanding of the decisions BHCs made regarding dividend and repurchase activity during the financial crisis. The charts in this post and the results of previous research provide some insight, but there is significant room to explore issues such as concerns about signaling financial weakness during a time of uncertainty, the role of herding behavior in the timing and extent of dividend reductions, and the relative impact of market-wide versus firm-specific factors in decisions to cut back on stock repurchases. And, looking ahead, supervisory oversight via the CCAR and the adoption of new regulatory capital standards that explicitly require reductions in capital distributions as regulatory capital ratios fall below certain trigger points will significantly affect BHCs' decisions about capital distributions. In sum, it is important to consider both dividends and stock repurchases in order to understand the impact of capital distributions on the banking industry, since large BHCs actively use both to manage their capital and distribute cash to shareholders.
~~~ Disclaimer |
| You are subscribed to email updates from The Big Picture To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |















0 comments:
Post a Comment